What is Multi-Factor Authentication
Since the dawn of multiple user computer systems, we’ve used passwords to prove to computers that we are who we say we are. But, passwords are just one way we can assert our identity to a computer. Security experts generally recognize a few categories of identity assertion, something you know, something you have, something you are, even somehwere you are.
Passwords fall into the something you know category, but this could also be a pass phrase, a PIN number, or a geusture. Basically, anything you store in your brain and can then communicate to the computer. Something you are is any kind of identifiable biometric. These are fingerprints, retinal-scan, even gait. Somewhere you are could rely on verifiable GPS or computer IP (Internet addresses) to assert that you’re in a location that’s acceptable. For example, your employers network resources may only be accessible if you’re on the WiFi in your office and many Internet services use Geographical restrictions to prevent access from other countries.
For the purposes of this article, we’ll focus in on the something you have category. Most commonly, when speaking about “multiple-factor” or “two-factor” authentication for personal use, the two factors in play are almost always a password or PIN and some form of something you have. In other words, to prove to the computer that you are who you say you are, you’ll not only type a password, but also use some method to verify that you have a thing that only you should generally have.
Why Use a Second Factor?
Passwords are rife with usability issues. The advice for their usage is nigh impossible to follow. Make sure they’re long. Like 16 letters, please. Random? Yes! Super random. With lots of symbols and numbers and things. So, some garbage like this…
n7KX*Bwao7#*lE$O
Oh! And make sure not to use it for more than one web site, so times that by like 50 or something.
Even clever tricks for making long passwords memorable, like using three random word passphrases, don’t stand up to the maths. And, even if you have a long, random gibberish password, if someone manages to read it from the post-it you’ve written it down on, the game is over. (An aside, this article isn’t about password managers. But you should definitely start using one. I like LastPass)
So, passwords have a terrible user experience, and because of that, folks use bad ones or manage them poorly. So, a second factor, like something you have, can take even a mediocre password and vastly improve your authentication set up.
Something You Have Factors, Ranked
There are a number of items you could have, that for the most part only you would have on your person. Some are special electronic devices specially tailored for this purpose, but the most common is your smart phone. Here, I’ve listed some of the common approaches for asserting that you have something only you should have, ranked from, in my opinion, best to worst.
1. U2F
U2F, Universal Two Factor, is a standard for interracting with a small, electronic, cryptographic piece of hardware that can be connected to a computer or smart phone via USB, Bluetooth, or NFC. Simply put, it’s a tiny electronic device that has a secret on it that’s nigh impossible to take off of it. If you plug it into your computer, you can register it with lots of online services and then later use it to prove that you are you.
U2F can be a tad intimidating at first as you have to overcome the “buy” button and put down at least $20 to bring it into your life. But, it is by far the best something you have option. Because of the nature of the technology, it’s among a few options for identification that cannot be phished. It also requires minimal interraction from the user to work, so the experience tends to be very convenient.
Yubico sells security keys online for as low as $20. The cheap version should work for most people. However, the nano versions offer a particularly convenient leave-in option. There are also NFC and Bluetooth options for mobile security.
2. App with Push Notification
Some online services offer a second factor through the use of a smartphone app. The app notifies you via push notification when you attempt to log in and all you have to do is hit a button to say “yes, that’s me trying to log in”. This proves that you have the device that the app is installed on, you can access the device, and you’ve logged into the second factor app on the device.
Google supports this style of second factor for their services with the Google app on iOS and Android. DUO provides such functionality for many other services on the web.
Similar to U2F, app based second factor of this type is not prone to phishing since any identifying information flows over a side-channel, your phone connection instead of your browser.
3. TOTP
TOTP, Time-based One Time Password, relies on a shared secret between you and the service you’re accessing that’s used to generate a new 6-digit pass-code every minute. Once you’ve loaded the secret from the service into your smartphone you can provide the rotating 6-digit code to prove that you have access to the device.
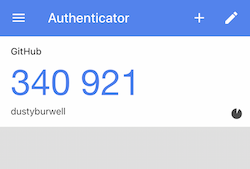
This is a fairly common and well supported form of second factor. The implementation is standardized and supported by several apps on iOS and Android including Google Authenticator and Authy. It’s very similar in concept to the historically well respected RSA security tokens.

The biggest ding against TOTP, however, is that the implementation generally involves a user typing the code into their browser which makes it imminently phishable. That said, used in conjunction with the LastPass browser extension, LastPass Authenticator can perform domain verification and automatically fill in pass codes for some web sites requiring that the user simply press a button on their mobile device to log in, providing some phishing prevention.
4. SMS
Many services will send you an authentication code to a mobile phone via SMS. Typing in the code shows that you maintain access to the SMS inbox for the given phone number. This form of second factor is wildly popular and implemented by popular web sites and is also the standard second factor for loads of banks and financial institutions.
Don’t be fooled, while SMS is easily the most common form of second factor, it is no where near the gold standard for security. There are known vulnerabilities in the global telephony infrastructure that allow for SMS interception and SIM swap social engineering attacks have become a regular feature of attacks on politicians and celebrities. SMS is also subject to the same phishing concerns as TOTP.
That said, SMS second factor is easy, and is certainly better than no second factor. For the majority of users, or where SMS is the only option, it’s worth setting up. But, for your high value accounts, email and banks in particular, prefer something up list.
Conclusion
Regardless of the type of second factor you use it really is imperative to set it up for any services or accounts that are of particularly high value to you. This certainly should include your email and bank accounts, as well as any services that are core to running your business. Using a second factor for authentication will take your personal security to the next level.